This afternoon,I'm knocking Code,Then on the west coast, a vps sent e-mail,Said server to restart Update,And I happen to have a vps is there in his。In addition to hardware and general maintenance accident,Cloud services basically online - after all,“High availability"It is the main subject of cloud services。
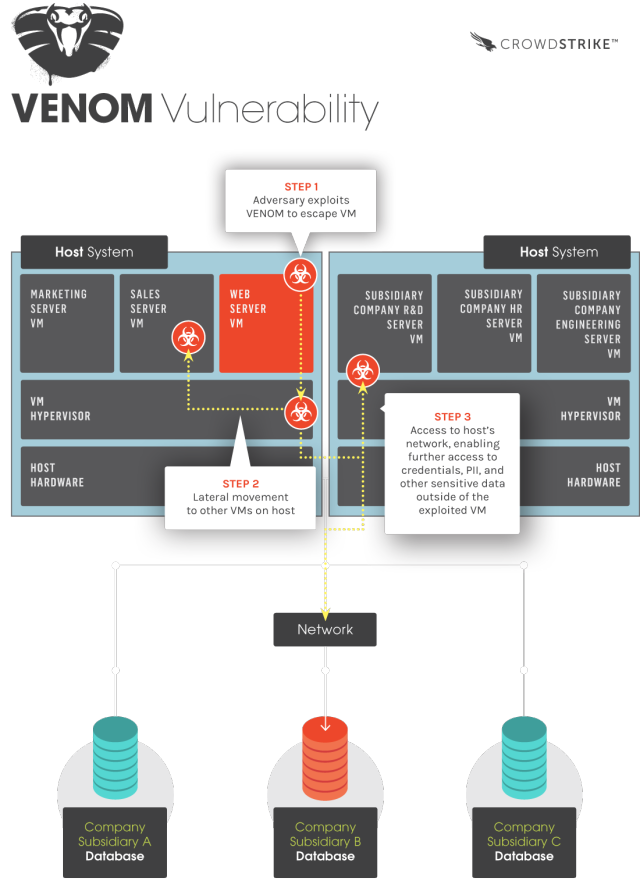
but,This time is different,Just today,The new virtual machine loopholes available,Exploit this vulnerability,You can make every minuteBreakthrough virtual machine restrictionsAnd get to the other servers in the same server access! Then use the information to other servers,And then we can continue to penetrate deep,Until the final data center!
All use There Xen KVM QEMU virtual platform users and users are affected by this vulnerability,Because of this vulnerability is on the floppy disk controller QEMU,That isWhether Linux、osx or Windows,As long as they run on the same server,You will be caught!
CrowdStrike It is a foreign security agencies,They first discovered this vulnerability:
According to their presentation page(See footer)Said time being have not seen anyone on the Internet takes advantage of this loophole -But I'm in a room where vps domestic situation encountered strange entire room is used for DDOS,Probably this loophole now looks。
principle
This vulnerability from the QEMUVirtual floppy disk controller,This code has been cited and many well-known virtual platforms so you know ......,Using QEMU are captive,For example, Xen,Such as KVM,of course,There QEMU yourself。In short,This floppy thing Although today's young people may not necessarily have seen it,And the computer will no longer provide this stuff - but you create a virtual machine, when this thing will still be loaded into the system default。and,For Xen and QEMU,Even if you manually disable the floppy drive,But there are still loopholes in the code that can be exploited by attackers。
The virtual machine operating system by sending a query、Read、Write、Formatting commands to access the floppy disk controller(FDC)。For FDC input and output ports,Virtual FDC QEMU uses a fixed size buffer to store data related to these commands and parameters。FDC to continuously monitor how much data is expected for each command,After the data is expected to take all of the commands have been received virtual machine,FDC Run and empty the cache waits for the next instruction。
Cache will be reset immediately after the completion of all commands executed FDC,In addition to two defined command。An attacker can send commands from the virtual machine and carefully modified data parameters to the FDC,Let it overflow data cache and execute arbitrary code in which the process server environment。
range
In addition to using QEMU virtual machine and platform,For example, VMware, Microsoft Hyper-VEtc. This class does not use QEMU platform and are not affected by this vulnerability。
function
Because of loopholes in the code is located on the virtual hardware controller,So long as it is supported by the operating system floppy captive:Windows、Linux、osx will all be put right,remember,Is a directGet root / administrator privileges!
patch
The relatively well-known service providers have released patches or documentation:
- QEMU: http://git.qemu.org/?p=qemu.git;a=commitdiff;h=e907746266721f305d67bc0718795fedee2e824c
- Xen Project: http://xenbits.xen.org/xsa/advisory-133.html
- Red Hat: https://access.redhat.com/articles/1444903
- Citrix: http://support.citrix.com/article/CTX201078
- FireEye: https://www.fireeye.com/content/dam/fireeye-www/support/pdfs/fireeye-venom-vulnerability.pdf
- Linode: https://blog.linode.com/2015/05/13/venom-cve-2015-3456-vulnerability-and-linode/
- Rackspace: https://community.rackspace.com/general/f/53/t/5187
- Ubuntu: http://www.ubuntu.com/usn/usn-2608-1/
- Debian: https://security-tracker.debian.org/tracker/CVE-2015-3456
- Suse: https://www.suse.com/support/kb/doc.php?id=7016497
- DigitalOcean: https://www.digitalocean.com/company/blog/update-on-CVE-2015-3456/
- f5: https://support.f5.com/kb/en-us/solutions/public/16000/600/sol16620.html
(List of connections from CrowdStrike)
This and other virtual machines through the loopholes in what is the difference?
A difference,Here CrowdStrike It includes a number of other virtual machines through the loophole:
- CVE-2007-1744 – Directory traversal vulnerability in shared folders feature
- CVE-2008-0923 – Path traversal vulnerability in VMware’s shared folders implementation
- CVE-2009-1244 – Cloudburst (VMware virtual video adapter vulnerability)
- CVE-2011-1751 – Missing hotplug check during device removal
- CVE-2012-0217 – 64-bit PV guest privilege escalation vulnerability
- CVE-2014-0983 – Oracle VirtualBox 3D acceleration multiple memory corruption vulnerabilities
Specifically I will not translate,Want to know more friends read for yourself:
Further reading
Extremely serious virtual machine bug threatens cloud providers everywhere
VIRTUALIZED ENVIRONMENT NEGLECTED OPERATIONS MANIPULATION
Original article written by LogStudio:R0uter's Blog » VM most serious vulnerabilities Venom cloud services is threatened!
Reproduced Please keep the source and description link:https://www.logcg.com/archives/995.html