Update
Just this morning,Apple released version 10.9.2 update,大小 859.7M,If you do not brush out of the AppStore update,Do not worry,Go to the official website to downloadNow!
Foreword
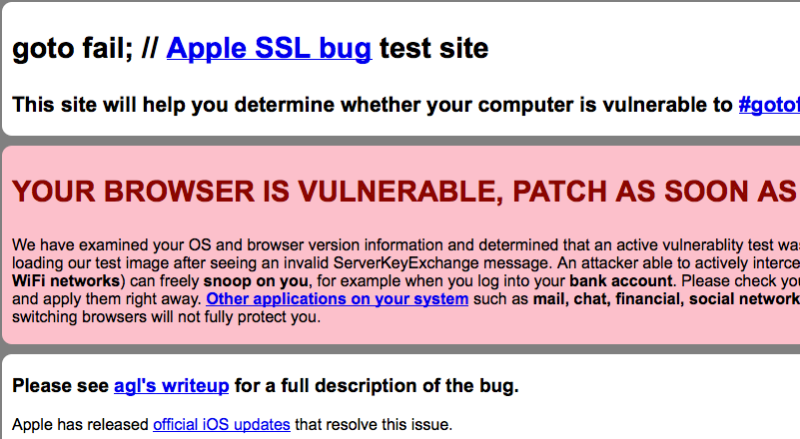
Just two days ago,Apple Push the latest version of iOS7.0.6,The good news is not blocked escape vulnerability on。Of course,The update does not change anything else,That fixes a vulnerability。What is the vulnerability has been calm this predicament usually make Apple such a large campaign do? That is SSL connection is established bug,This bug causes SSL to bypass the verification step directly during verification,Simply put,It is,,,Uh,,,Can verify success anyway。Prone to third-party attacks。SSL is widely used in the network,So this security level is not generally high。The official page is here http://support.apple.com/kb/HT6147
influences
This vulnerability not only affects the iOS system of Apple’s phones and tablets,And your computer! If you are using a Mac, use the latest OS X10.9 operating system,Then,You are exposed to this loophole,But computer and laptop users are not so lucky,Ok,In official terms, the patch will be given "as soon as possible"... so,If you are using OS X 10.9,Latest operating system,You are used to using Safari browser,It is best to pay attention to the progress of the patch about this vulnerability~
Actually,The impact of this vulnerability is far more than just Safari,For details, please visit this article of the open source Chinese community:"SSL/TLS connection verification issues seriously affect OS X"
verification
accessThis pageYou can verify whether your browser is exposed to this vulnerability,If the page in this article appears,Congratulations on your winning。
Other than that,You can also try to visitThis page,If you see the text,That also means that you are exposed to the vulnerability,After patching the vulnerability,You should not be able to open this page,and,You will be prompted that SSL verification failed。
patch
Until now,There is still no news about the official patch for OS X,So a great god wrote a temporary patch and posted it online,I believe that many children's shoes know this patch,I just don't know how to use it,Here is the route to write about the use of this patch。
Scope of application
[warning]
- This temporary third-party patch only applies to 10.9 64-bit software,32Bit invalid;
- This patch is a temporary experimental patch,Like jailbreak,At your own risk;
If you are not exposed to the public WiFi environment often,Generally, you only use your computer at home (the local area network you are in is safe). It is estimated that this patch is useless (it only works for public WiFi environments)。- Actually,This vulnerability has far-reaching impact,As for this patch,Routing isRecommend everyone to signof,See"SSL/TLS connection verification issues seriously affect OS X"
[/warning]
step
Download the patch file
[Downlink href=”http://download.suhosin.org/APPLE_SSL_SECURITY_FRAMEWORK_QUICK_AND_DIRTY_64BIT_FIX.bspatch”]i0n1c’s bspatch file[/Downlink]
Use the following commands in turn to apply the patch
|
1 2 3 4 5 6 |
cd /System/Library/Frameworks/Security.framework/Versions/A sudo cp Security Security_bkup //备份原文件 sudo bspatch Security_bkup Security //在这句后边加个空格, //然后把下载的补丁文件拖进来再回车 |
Then restart your computer,Visit the two previous verification sites to try again~
Should be done。
Original article written by LogStudio:R0uter's Blog » Sign manually to your OS X patches marked with SSL
Reproduced Please keep the source and description link:https://www.logcg.com/archives/477.html