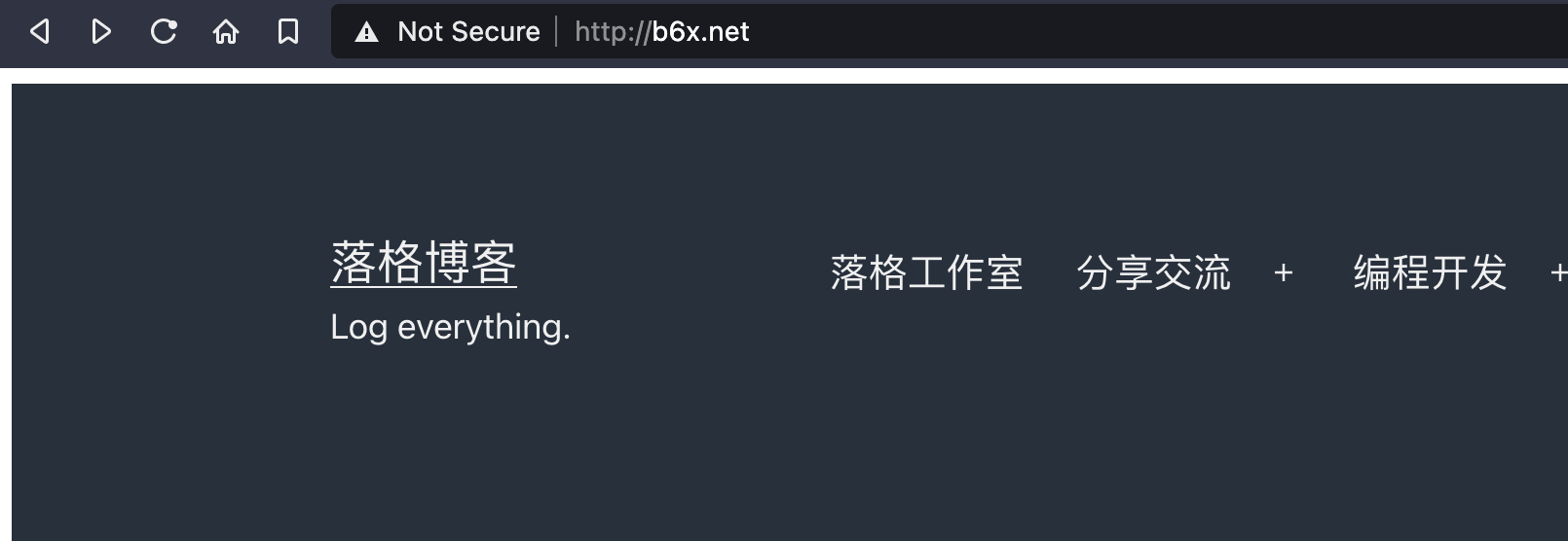
I accidentally found a batch of websites today,Such as http://b6x.net/ Now when you click on this website, it will display "www.logcg.com refused to connect.”,When I clicked on it for the first time, I was stunned...he actually copied my entire website? !
This is a series of three-digit domain name websites,Are similar operations。
Wait a minute,I found something wrong,First of all, there is a white box on the outside of this website that my blog does not have... that is,This may be an anti-generation (reverse proxy)。
If you still don’t know what anti-generation is,look at thisOn the forward proxy reverse proxy transparent proxy
So I checked this domain name,Located in Alibaba Cloud,Contact information is protected by the domain name of the service provider who originally purchased the domain name,The resolved ip address is the cdn address,Of no use。I try to block with a domain name,As a result, people still showed it well...
During this process,I found out a little more:If it is a reverse proxy,The domain name links in the website should be relayed by the agent,And in this website,The link to my blog has not been modified in any way,Is my original domain name。
View the source code of the page to discover,In fact, this website has only one line of code:
|
1 |
<iframe width="100%" height="100%" frameborder="0" align="center" allowfullscreen="true" allow="autoplay" id="iframe" src="https://www.logcg.com/"></iframe> |
That is,When you open this website,It loads R0uter's blog in its own page......
of course,This seems harmless,But there are many potential security issues,For example, he can do transparent clickjacking and so on... Besides, I don’t know the webmaster of this domain name。To avoid this,Need to modify nginx configuration,Add an http header add_header X-Frame-Options "SAMEORIGIN";
of course,You have other options,such as DENY Is to reject all behaviors that are embedded in other web pages;SAMEORIGIN Is a convenient option,What if you want to embed your own? As long as it is the same domain source,You can allow,No one else;ALLOW-FROM URI This option is the basic whitelist function,Who wrote,Who can embed without being rejected。
Here we use SAMEORIGIN,The add_header X-Frame-Options "SAMEORIGIN"; Write it in your server configuration,Restart Service。
For example, there are 3 items in my place after modification:
|
1 2 3 |
add_header Strict-Transport-Security max-age=15768000; add_header Access-Control-Allow-Origin *; add_header X-Frame-Options "SAMEORIGIN"; |
Then refresh that http://b6x.net/ ,It's already blank。
References
- Check the website,Clickjacking found:X-Frame-Options is not configured,Solution
- Secure Nginx from Clickjacking with X-FRAME-OPTIONS
Original article written by LogStudio:R0uter's Blog » Avoid website hijacking by malicious domain names
Reproduced Please keep the source and description link:https://www.logcg.com/archives/3507.html

Singularity Information
Singularity Information,Singularity Information,Singularity Information,Singularity Information,Singularity Information,Singularity Information
very useful guide,learned
It seems that the rss feed was deleted by mistake, right?
I can’t link the tt-rss。
[16:30:41/85472] fetch error: LibXML error 63 at line 694 (column 814): CData section not finished
There should be some problems with the following sentence。
<![CDATA[go withR0uter's BlogRead the fully formattedAvoid website hijacking by malicious domain names
I feel it should be a problem with the rss optimization plug-in,Because I wrote this sentence in the plugin,Let me try to add parentheses... emmmmmm
Or not,It shouldn't be a matter of parentheses,I took a look,Line 694 in your rss,^M like this,You can bind successfully。There is an extra ^M symbol in it。I can’t see it with a browser,Text editor,Don't know what edit you use,It can be seen with emacs。 It should be fine to delete this。
emmmmmmm,This bug seems to be plug-in,But I actually found this invisible symbol... it's in https://www.logcg.com/archives/3456.html Inside,It seems that a character was cut by mistake。Do you have any questions? Thank you so much~
It's okay,But I can’t reply below your last comment,Reply here。
👌
Learned 3q!
Many methods,Judge referer、Content-Security-Policy、JS judgment is fine
Took a look at mine,Oh don't be afraid
add_header Strict-Transport-Security “max-age=63072000; includeSubDomains; preload”;
add_header X-Frame-Options “SAMEORIGIN” always;
add_header X-Xss-Protection “1; mode=block” always;
add_header X-Content-Type-Options “nosniff” always;
add_header Content-Security-Policy “default-src https: ‘unsafe-inline’ ‘unsafe-eval’ data:;”;
add_header Referrer-Policy “no-referrer-when-downgrade”;
You have more dicks than mine,Gangster!
I also looked at the domain name on a whim,Then come out five or six such websites,Now they can't open it hahaha
Hahahaha you need this website https://securityheaders.com/
Too difficult 😭