Update:upgrade Ubuntu 20.04 LTS Rear,csf is not working,Prompt that iptables cannot be found:
|
1 |
Testing ip_tables/iptable_filter...open3: exec of /sbin/iptables -I OUTPUT -p tcp --dport 9999 -j ACCEPT failed: No such file or directory at /usr/local/csf/bin/csftest.pl line 144. |
This is because Ubuntu 20.04 LTS Changed iptables Related command position,The csf script is not updated in time。
|
1 |
/sbin/iptables → /usr/sbin/iptables |
To solve this problem,We can go to /etc/csf/csf.conf Profiles,Near the end of this file,Have a # Binary locations Related settings,Here we can see that the first 6 configuration addresses are still old:
|
1 2 3 4 5 6 7 8 |
# Binary locations IPTABLES = "/sbin/iptables" IPTABLES_SAVE = "/sbin/iptables-save" IPTABLES_RESTORE = "/sbin/iptables-restore" IP6TABLES = "/sbin/ip6tables" IP6TABLES_SAVE = "/sbin/ip6tables-save" IP6TABLES_RESTORE = "/sbin/ip6tables-restore" …… |
Change to new address:
|
1 2 3 4 5 6 7 |
# Binary locations IPTABLES = "/usr/sbin/iptables" IPTABLES_SAVE = "/usr/sbin/iptables-save" IPTABLES_RESTORE = "/usr/sbin/iptables-restore" IP6TABLES = "/usr/sbin/ip6tables" IP6TABLES_SAVE = "/usr/sbin/ip6tables-save" IP6TABLES_RESTORE = "/usr/sbin/ip6tables-restore" |
Such, csf -r You can generate the configuration normally,but,weakness is perl /usr/local/csf/bin/csftest.pl Will still report an error,But now csf itself has been successfully started。
Before I wrote an article,After purchasing a VPS you should spare security measures,This side describes how to install csf Firewall,In fact, just a few simple commands,but,At that time, my ignorance,In fact lead to csf firewall does not really take effect,The reason is csf and ufw are the same as iptables script,They are in the same level,We are conflicting。
so,In the configuration csf Firewall,You should execute the command ufw disable To close ufw。
then,We installed a firewall csf:
|
1 2 3 4 |
wget https://download.configserver.com/csf.tgz tar -zxvf csf.tgz cd csf sh install.sh |
After the installation is complete,Install environmental needs:
|
1 |
apt install libwww-perl perl sendmail |
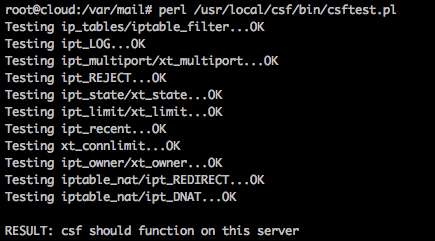
After ok,Execute commands to check the status of the firewall: perl /usr/local/csf/bin/csftest.pl ,If the output is as follows,Then the implementation of the firewall should be no problem:
First of all we have to do the most basic configuration,To configure the release port of csf,I must remember not to 22 Port to cut off,Otherwise, you good-bye。
of course,Once installed csf,The default is to release common port,so,We do not just get rid of。Other,csf default working in test mode,So if you really put himself out of the,It's ok,Five minutes later emptied rules。
Let's edit we /etc/csf/csf.conf :
by default,Following the release of the port:
|
1 2 3 4 5 6 7 |
TCP_IN = "20,21,22,25,53,80,110,143,443,465,587,993,995" TCP_OUT = "20,21,22,25,53,80,110,113,443" UDP_IN = "20,21,53" UDP_OUT = "20,21,53,113,123" |
Here I am according to my needs,Made to streamline:
|
1 2 3 4 5 6 7 8 9 10 11 12 |
# Allow incoming TCP ports TCP_IN = "22,80,143,53,443" # Allow outgoing TCP ports TCP_OUT = "22,25,53,80,110,113,443,587,993,995" # Allow incoming UDP ports UDP_IN = "53" # Allow outgoing UDP ports # To allow outgoing traceroute add 33434:33523 to this list UDP_OUT = "53,113,123,33434:33523" |
of course,My server also supports IPv6,It is necessary to continue to turn down,Find the IPv6 configuration,do it again:
|
1 2 3 4 5 6 7 8 9 10 11 12 |
# Allow incoming IPv6 TCP ports TCP6_IN = "22,80,143,53,443" # Allow outgoing IPv6 TCP ports TCP6_OUT = "22,25,53,80,110,113,443,587,993,995" # Allow incoming IPv6 UDP ports UDP6_IN = "53" # Allow outgoing IPv6 UDP ports # To allow outgoing traceroute add 33434:33523 to this list UDP6_OUT = "53,113,123,33434:33523" |
Then add defense rules,Prevent a small amount of daily ddos,of course,Then had to rely on a large amount of hardware, right?
Find the field PORTFLOOD ,Make the following rules:
|
1 |
PORTFLOOD = "22;tcp;5;300,80;tcp;20;5,443;tcp;20;5" |
Here are the rules say each port 22,80,443Do strategy (IP-units):
- in case 22 In an IP port 300 Initiated within seconds 5 Or more links,To ban;
- in case 80 or 443 In an IP port 5 Initiated within seconds 20 Or more links,To ban。
ban time default 1800 second。
then,csf there is a function of email to inform you that after the ban of the IP,We make changes to the following fields,Add your own e-mail address:
|
1 |
LF_ALERT_TO = "your-email@gmail.com" |
Since lfd also sends suspicious process monitoring,If you feel tired,The process can advance your whitelist,edit /etc/csf/csf.security ,Following the end of the supplement format on it,For example, I run a server nginx,php,I know it's not suspicious process,Then write:
|
1 2 |
exe:/usr/sbin/nginx exe:/usr/sbin/php-fpm7.0 |
Such,We configured the firewall,Save the configuration after wave can try restarting:
Remember to view the configuration is correct with a sense command: perl /usr/local/csf/bin/csftest.pl
Then use the command csf -r To restart the firewall,If no fatal problem,It means that the firewall work。As for the phrase:
|
1 |
*WARNING* RESTRICT_SYSLOG is disabled. See SECURITY WARNING in /etc/csf/csf.conf. |
Let him disabled .。
Another problem you might encounter,That prompted you to start but crashed lfd,this is normal,In test mode, lfd does not start。
re-edit /etc/csf/csf.conf Profiles,In the first line,The 1 To 0:
|
1 |
TESTING = "0" |
After saving the restart firewall csf -r This time the firewall is up and running。
Use the command to start csf and lfd incidental:
|
1 2 |
service csf start service lfd start |
By looking at /where/log/Ser.log You can see all the acts csf firewall,For example, a ban which IP like。
If you want to add a whitelist,Then edit /etc/csf/csf.allow ,ip address one per line;
If you want to manually add blacklist,Then edit /etc/csf/csf.deny ,Is a line,but,This side will have regular data automatically added;
Other,You can also add the ignore list,IP address list will not be judge rules,But if there is in the blacklist,It will be blocked: /etc/csf/csf.ignore
Such,Your server should be a more robust :)
additional
Another point,If you are annoying email notifications,You can search for all in csf.conf _EMAIL_ALERT Ending field,Change the value from "1" To "0" ,There are several,Remember to use search。
References
CSF installation and configuration of the firewall on Ubuntu
How To Install and Configure Config Server Firewall (CSF) on Ubuntu
linux csf firewall to prevent a small number of very effective attack ddos cc
How to disable send an email: lfd on server: Suspicious process running under user
Original article written by LogStudio:R0uter's Blog » Csf firewall to effectively prevent the use of small-scale DDOS
Reproduced Please keep the source and description link:https://www.logcg.com/archives/2873.html
lfd.service – ConfigServer Firewall & Security – Ser
Loaded: loaded (/usr/lib/systemd/system/lfd.service; enabled; vendor preset: enabled)
Active: active (running) since Fri 2018-02-02 22:15:11 CST; 4s ago
Process: 28943 ExecStart=/usr/sbin/lfd (code=exited, status=0/SUCCESS)
Main PID: 28951 (Ser – sleeping)
Tasks: 1 (limit: 4915)
CGroup: /system.slice/lfd.service
└─28951 Ser – sleeping
Feb 02 22:15:10 VPS systemd[1]: Stopping ConfigServer Firewall & Security – Ser…
Feb 02 22:15:10 VPS systemd[1]: lfd.service: Main process exited, code=killed, status=9/KILL
Feb 02 22:15:10 VPS systemd[1]: Stopped ConfigServer Firewall & Security – Ser.
Feb 02 22:15:10 VPS systemd[1]: lfd.service: Unit entered failed state.
Feb 02 22:15:10 VPS systemd[1]: lfd.service: Failed with result ‘signal’.
Feb 02 22:15:10 VPS systemd[1]: Starting ConfigServer Firewall & Security – Ser…
Feb 02 22:15:11 VPS systemd[1]: Started ConfigServer Firewall & Security – Ser.
Please help us to see this is what ah,How to deal with it,Thank you!
I thought you was a DDoS /(¨Ò o ¨Ò)/~~
It is a ddos,Restart a wave of good。I may be a little less now server performance,So a bit of a hit on the lost。