Recently more and more high wall,With the relationship between fascism and the moon cake festival,Many also demolished the ladder。Even developers are also several ladders?,So,In addition to "How science online," this issue,"How to stay safe online," this issue has become more and more people can not be ignored。
I know all of you not only to use,It is a general use computer access,I think this issue should also receive attention。Everything you say in the network above all by your service provider、ISP unavoidably record ...... It was originally a good purpose - once over the network thugs attack,We can quickly arrested him - but,Once this information fall into the wrong hands,That would be disastrous。
Generally, we would like,What's that history has something important to do? As long as my account password secure enough ah! Actually,It is these information,An opportunity to hackers。Your these materials,Will becomeSocial engineeringCreative attack。
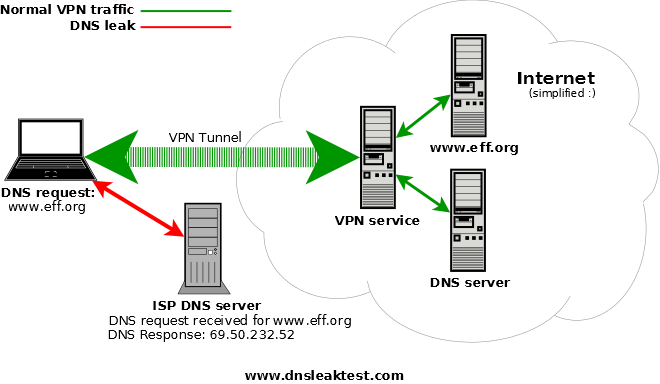
So what is it DNS leak?
Use the Internet browser,Enter your domain name will depend on DNS to translate IP address - the computer can not know what is a domain name。so,You may access the contents through the https encryption,But the same ISP can record what you visit those sites!
Even if you use a proxy to access the network and VPN,Your DNS may still be resolved locally,This will cause your hidden whereabouts becomes meaningless! - This is the number one threat to personal privacy:DNS leak。
For now,When you use a VPN when,DNS should be resolved remotely,However, some providers do not support it;Also, if you usesocksproxy,Then only 5 SupportedRemote DNS resolution
Other than that
If you use a pac,Then you need aAccording to the domain nameTo choose instead of the IP proxy pac。- Because it will still be parsed and then determine whether you need a proxy IP。
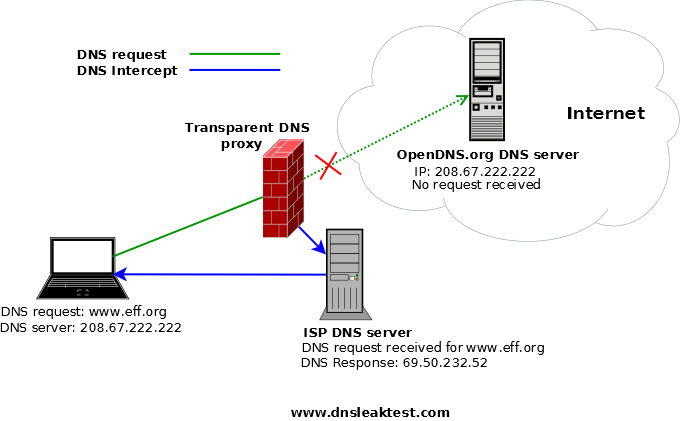
Otherwise,You may disclose the DNS:
DNS forwarding transparent
This time it was suggested,If you use a VPN,To avoid DNS poisoning (actually leaked a),To use a third party's public DNS service,For example, Google's 8.8.8.8 ,But if your DNS leaked,Even with public DNS will not help:
Do you think you access to a third party on a public DNS,In fact, you still visit the ISP's DNS server。
More details about the visit leaked DNS:https://dnsleaktest.com/what-is-a-dns-leak.html
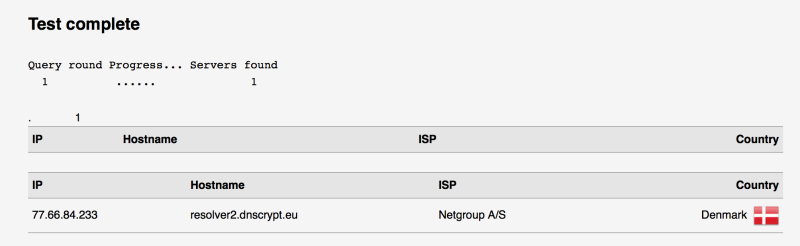
To test DNS leak,access:https://dnsleaktest.com
Use dnscrypt and dnsmasq
dnscrypt It is a project of the Open DNS,It allows you to encrypt access to DNS server,And parse domain name。If using https to access web sites。and dnsmasq It is a lightweight DNS server,We set up a local caching DNS to resolve it Reply,So we do not at the same time, repeated many times to resolve the same domain name - after all, than the plaintext encryption DNS resolution resolves quickly。
note
In fact, among the most Linux systems, dnsmasq is the default comes - it does not bloated,It will not consume much resources。
ready
In order to install and dnsmasq dnscrypt ,You need to install Xcode - we need to use Xcode comes with a number of command-line tools。
After installing Xcode,Use the command to install the Homebrew:
|
1 |
ruby -e "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)" |
It is similar apt-get or yum The package manager,Once it is installed,You may need the following settings:
Slow brew update image update source solutions
Install dnsmasq
use brew install dnsmasq To install it。
We edit its configuration:
|
1 2 3 |
mkdir -p /usr/local/etc cp /usr/local/opt/dnsmasq/dnsmasq.conf.example /usr/local/etc/dnsmasq.conf vim /usr/local/etc/dnsmasq.conf |
For example, the following configuration:
|
1 2 3 4 5 6 7 8 |
# Never forward plain names domain-needed # Never forward addresses in the non-routed address spaces bogus-priv # Forward queries to dnscrypt on localhost server=127.0.0.1#5355 |
Then write an additional configuration: echo "conf-dir=/usr/local/etc/dnsmasq.d" >> /usr/local/etc/dnsmasq.conf To make the configuration directory to put more rules take effect:
|
1 2 3 4 5 6 7 |
mkdir /usr/local/etc/dnsmasq.d //创建配置目录 wget -4 --no-check-certificate -O /usr/local/etc/dnsmasq.d/accelerated-domains.china.conf https://raw.githubusercontent.com/felixonmars/dnsmasq-china-list/master/accelerated-domains.china.conf //为国内常用网站取消DNS加密 |
For example, domestic Taobao, Jingdong such sites,I think you will not go Agent,So there is no need to deal with encryption,Because many domestic use cdn acceleration,We have foreign words will cause the DNS resolution went on an overseas line,Very slow。If you need to encrypt,This step can be skipped?。
Setting Start:
|
1 2 3 |
sudo cp -fv /usr/local/opt/dnsmasq/*.plist /Library/LaunchDaemons sudo chown root /Library/LaunchDaemons/homebrew.mxcl.dnsmasq.plist sudo launchctl load /Library/LaunchDaemons/homebrew.mxcl.dnsmasq.plist |
use sudo lsof -There is no UDP:53 or ps -if | grep '[d]nsmasq ' Dnsmasq has started to verify。
Although dnsmasq is used as the DNS cache,It is also generally used in micro-server such as a DHCP server on OpenWRT。In fact, it used more in this respect。But do not worry,dnsmasq default installation we do not open the DHCP function。
Installation dnscrypt
use brew install dnscrypt-proxy Install dnscrypt。
Setting Start:
|
1 2 |
sudo cp -fv /usr/local/opt/dnscrypt-proxy/*.plist /Library/LaunchDaemons sudo chown root /Library/LaunchDaemons/homebrew.mxcl.dnscrypt-proxy.plist |
Edit profile,The local address to listen 127.0.0.1:5355To cope with dnsmasq:
|
1 |
sudo vi /Library/LaunchDaemons/homebrew.mxcl.dnscrypt-proxy.plist |
exist <string>/usr/local/opt/dnscrypt-proxy/sbin/dnscrypt-proxy</string> Below this line insert: <string>--local-address=127.0.0.1:5355</string> ,Good to avoid conflict and dnsmasq dnsmasq and only allow access to it:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-/Apple/DTD PLIST 1.0/EN" "http:/www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>Label</key> <string>homebrew.mxcl.dnscrypt-proxy</string> <key>KeepAlive</key> <true/> <key>RunAtLoad</key> <true/> <key>ProgramArguments</key> <array> <string>/usr/local/opt/dnscrypt-proxy/sbin/dnscrypt-proxy</string> <string>--local-address=127.0.0.1:5355</string> <string>--ephemeral-keys</string> <string>--resolvers-list=/usr/local/Cellar/dnscrypt-proxy/1.6.0/share/dnscrypt-proxy/dnscrypt-resolvers.csv</string> <string>--resolver-name=dnscrypt.eu-dk</string> <string>--user=nobody</string> </array> <key>UserName</key> <string>root</string> <key>StandardErrorPath</key> //余下部分省略不写。 |
At last,use sudo launchctl load /Library/LaunchDaemons/homebrew.mxcl.dnscrypt-proxy.plist Start Service。
use sudo lsof -There is no UDP:5355 or ps -if | grep '[d]nscrypt' To verify that the service is already in force。
there is a corresponding dnscrypt dnscrypt-wrapper,It is compatible dnscrypt-proxy encryption - which means you can use it to build their own server without using public dnscrypt dnscrypt server。- This is used against DNS poisoning - you can refer to the end of "Further Reading" in the link to learn more。
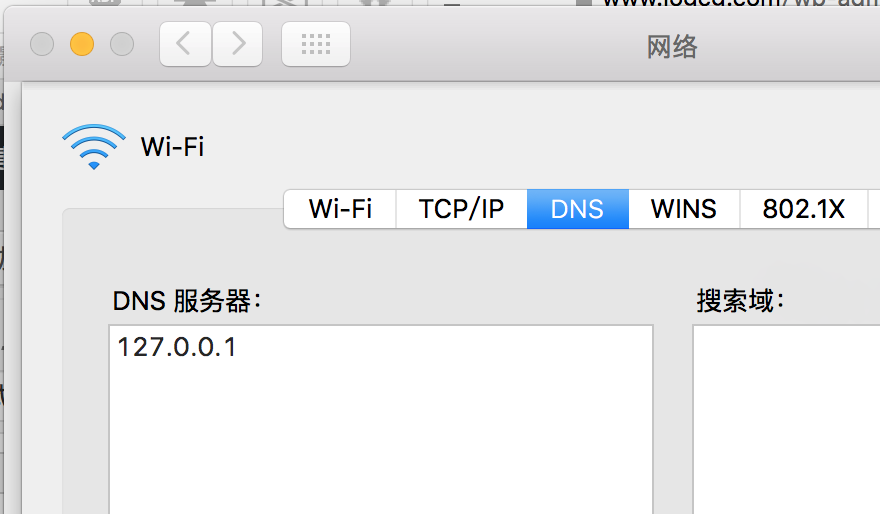
Network Configuration
turn on Preferences → Advanced → Network →DNSTab ,Only fill 127.0.0.1 And save it。
verification
Use dig to verify whether the two were working properly:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 |
╰─➤ dig www.twitter.com @127.0.0.1 -p 5355 ; <<>> DiG 9.8.3-P1 <<>> www.twitter.com @127.0.0.1 -p 5355 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 12542 ;; flags: qr rd ra; QUERY: 1, ANSWER: 5, AUTHORITY: 4, ADDITIONAL: 5 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.twitter.com. IN A ;; ANSWER SECTION: www.twitter.com. 490 IN CNAME twitter.com. twitter.com. 16 IN A 199.16.156.6 twitter.com. 16 IN A 199.16.156.102 twitter.com. 16 IN A 199.16.156.198 twitter.com. 16 IN A 199.16.156.230 ;; AUTHORITY SECTION: twitter.com. 112220 IN NS ns4.p34.dynect.net. twitter.com. 112220 IN NS ns2.p34.dynect.net. twitter.com. 112220 IN NS ns3.p34.dynect.net. twitter.com. 112220 IN NS ns1.p34.dynect.net. ;; ADDITIONAL SECTION: ns1.p34.dynect.net. 40536 IN A 208.78.70.34 ns2.p34.dynect.net. 40536 IN A 204.13.250.34 ns3.p34.dynect.net. 40536 IN A 208.78.71.34 ns4.p34.dynect.net. 40536 IN A 204.13.251.34 ;; Query time: 423 msec ;; SERVER: 127.0.0.1#5355(127.0.0.1) ;; WHEN: Wed Sep 2 21:10:55 2015 ;; MSG SIZE rcvd: 272 //你可能需要稍微等一会dnscrypt才能够建立连接。 |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 |
─➤ dig www.google.com @127.0.0.1 ; <<>> DiG 9.8.3-P1 <<>> www.google.com @127.0.0.1 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 6714 ;; flags: qr rd ra; QUERY: 1, ANSWER: 5, AUTHORITY: 4, ADDITIONAL: 5 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.google.com. IN A ;; ANSWER SECTION: www.google.com. 297 IN A 173.194.112.116 www.google.com. 297 IN A 173.194.112.112 www.google.com. 297 IN A 173.194.112.113 www.google.com. 297 IN A 173.194.112.114 www.google.com. 297 IN A 173.194.112.115 ;; AUTHORITY SECTION: google.com. 112253 IN NS ns3.google.com. google.com. 112253 IN NS ns2.google.com. google.com. 112253 IN NS ns1.google.com. google.com. 112253 IN NS ns4.google.com. ;; ADDITIONAL SECTION: ns1.google.com. 300608 IN A 216.239.32.10 ns2.google.com. 300608 IN A 216.239.34.10 ns3.google.com. 300608 IN A 216.239.36.10 ns4.google.com. 300608 IN A 216.239.38.10 ;; Query time: 519 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Wed Sep 2 21:10:22 2015 ;; MSG SIZE rcvd: 259 //第一次查询略慢,因为要走dnscrypt。 ╰─➤ dig www.google.com @127.0.0.1 ; <<>> DiG 9.8.3-P1 <<>> www.google.com @127.0.0.1 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 64399 ;; flags: qr rd ra; QUERY: 1, ANSWER: 5, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;www.google.com. IN A ;; ANSWER SECTION: www.google.com. 105 IN A 173.194.112.116 www.google.com. 105 IN A 173.194.112.115 www.google.com. 105 IN A 173.194.112.114 www.google.com. 105 IN A 173.194.112.113 www.google.com. 105 IN A 173.194.112.112 ;; Query time: 0 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Wed Sep 2 21:13:34 2015 ;; MSG SIZE rcvd: 112 //注意查询时间为0,以后的一段时间内,DNS就被缓存了:) |
Further reading
Compile and install anti-pollution dnscrypt-wrapper build DNS server
Privacy & Security Guide on OS X
Original article written by LogStudio:R0uter's Blog » Avoid DNS leaks on OS X
Reproduced Please keep the source and description link:https://www.logcg.com/archives/1311.html
magnificent submit, very informative. I wonder why the opposite specialists of this sector do not understand this. You must proceed your writing. I’m confident, you have a great readers’ base already!
Now there is a stubby (DNS-over-tls) https://github.com/getdnsapi/stubby Good use of tools,It is also simple with
Really good,I look back to write articles 😏
Now there is a stubby https://github.com/getdnsapi/stubby Very good use,It is also equipped with convenient
Are launchctl load can then open another instance dnscrypt it?
For example, I would like to use the two lines corresponding to two ports
127.0.0.1:5301 — cisco
127.0.0.2:5302 — fvz-rec-hk-ztw-01
Theoretically possible,You need to copy plist,Then get rid of the port,This should be able to start two instances,I have not tried,If this is not,That should not alright,Try it yourself。
Another method is to use docker from service,In this case since several are ok。
Or write the script with the traditional way of linux :)
macOS latest system execute sudo launchctl load /Library/LaunchDaemons/homebrew.mxcl.dnscrypt-proxy.plist do not start to take effect,But I can access through google shadowsocksx、facebook,What happens then?Executive dig http://www.google.com @127.0.0.1 -p 5355也是connection timed out; no servers could be reached,But you can access
Find the reasons,Above 1024 mac does not open,In other ports like less than 1024,Thanks for Bloggers