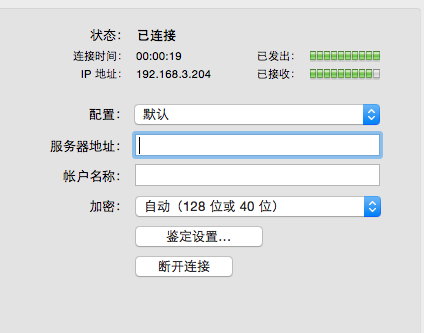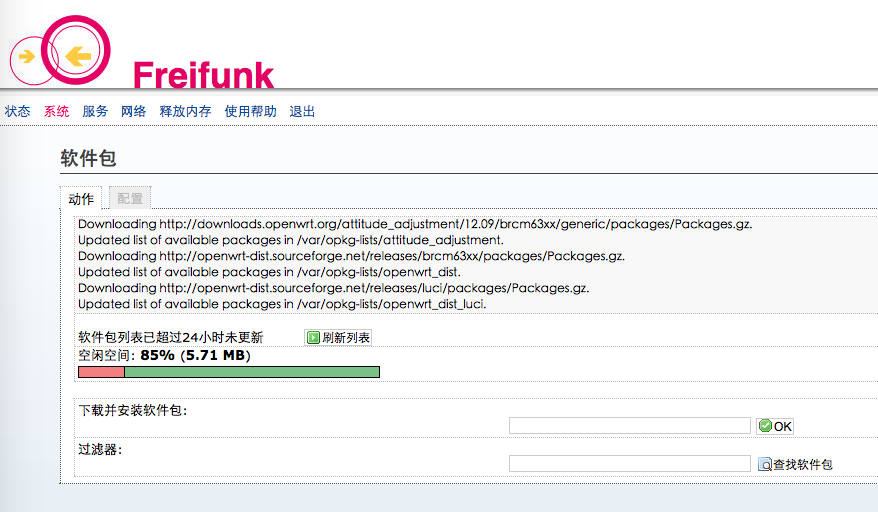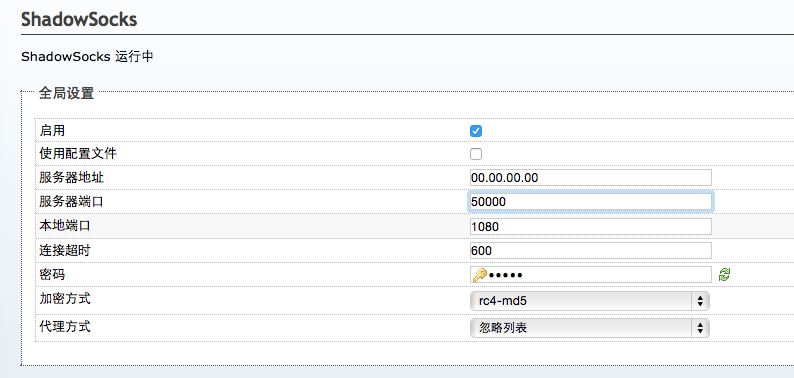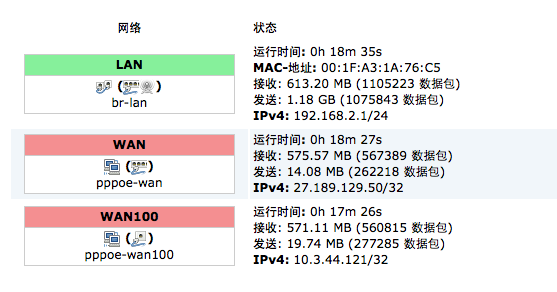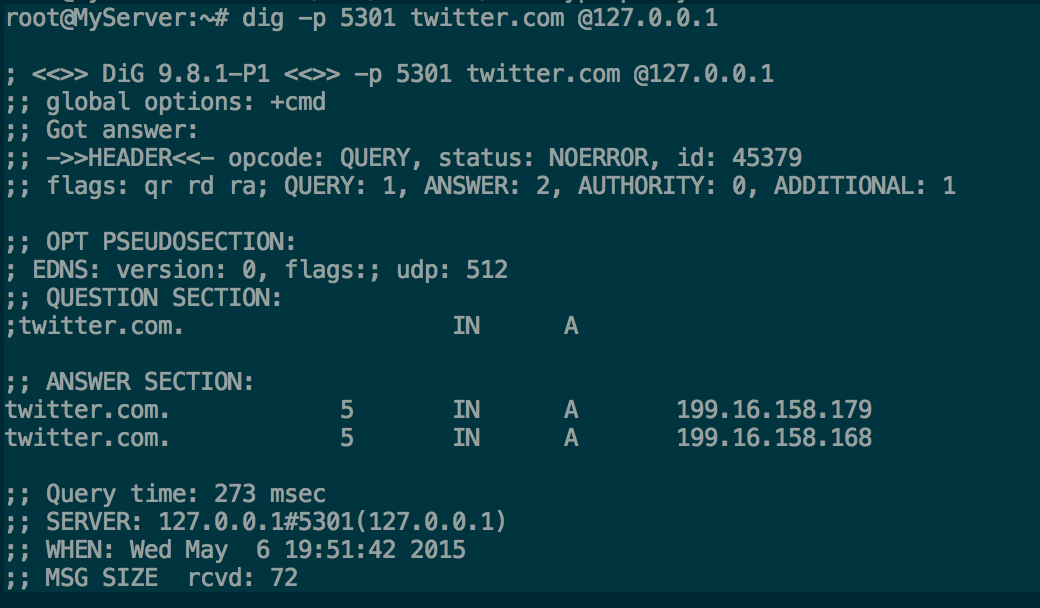
All to known,I want to get them abroad towards LAN DNS information,Will certainly suffer keywordPollution。to this end,Some people thinkUse exception port,For example, instead of using 5353 as the current DNS dedicated port 53-- Girl Friend Wall Only 53 pollution;It was also thought of using a TCP connection request,Because DNS response mechanism(参考 DHCP)I decided itaccept[……]